This article was first published on Deythere.
- Disguised to be a Genuine Wallet But Malicious Inside
- The Stealth Attack: Sui Encodes The Seed Phrase
- Why It Went on So Long: Failures in Chrome Store Vetting
- How Users Were Warned and What They Can Do
- A Warning for the Crypto Ecosystem
- Conclusion
- Glossary
- Frequently Asked Questions About Chrome Wallet Scam
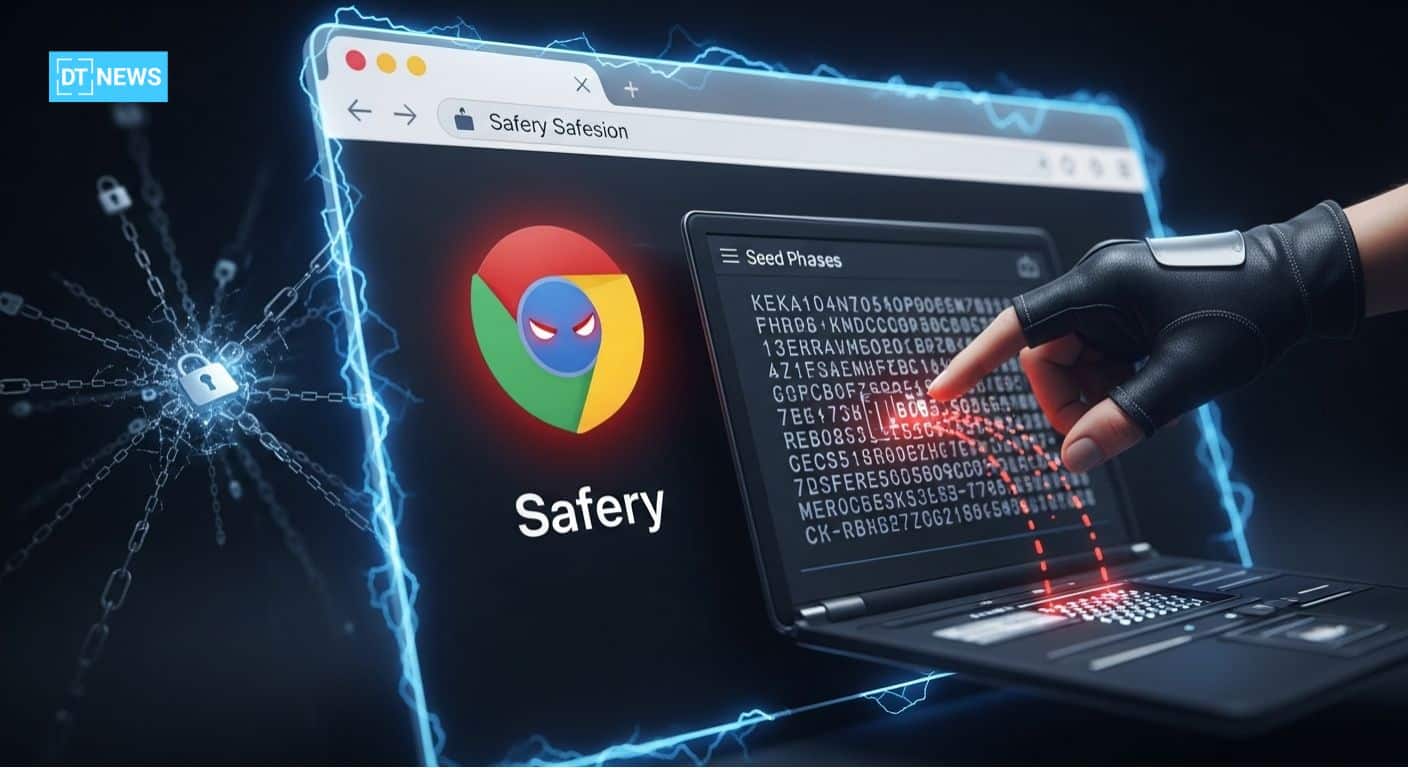
A seemingly legitimate Chrome extension dubbed “Safery: Ethereum Wallet” has been caught stealing users’ seed phrases in the background.
Instead of servers or classic phishing, the extension had stored mnemonic phrases using tiny on-chain transactions on Sui coded in a way that made it feel like everyone had been robbed virtually unnoticed.
The insidiousness of these smart contracts enabled attackers to piece together the wallet recovery phrases of users and deplete their assets. This Chrome wallet scam exposes a new attack vector that abuses the blockchain itself to enable data exfiltration.
Disguised to be a Genuine Wallet But Malicious Inside
The “Safery: Ethereum Wallet” app resembled the kind of neat, safe and secure wallet users would want to store money in.
It showed up in the Chrome Web Store as one of the top search results for “Ethereum wallet,” alongside popular browser extensions like MetaMask, Wombat and Enkrypt.
Its publisher page was minimal, the description focused on security and it claimed to store keys locally giving a perception that users were dealing with something safe.
The extension even requested to work on all websites, a permission that is common for wallet extensions, so there weren’t obvious alarms going off for typical users.
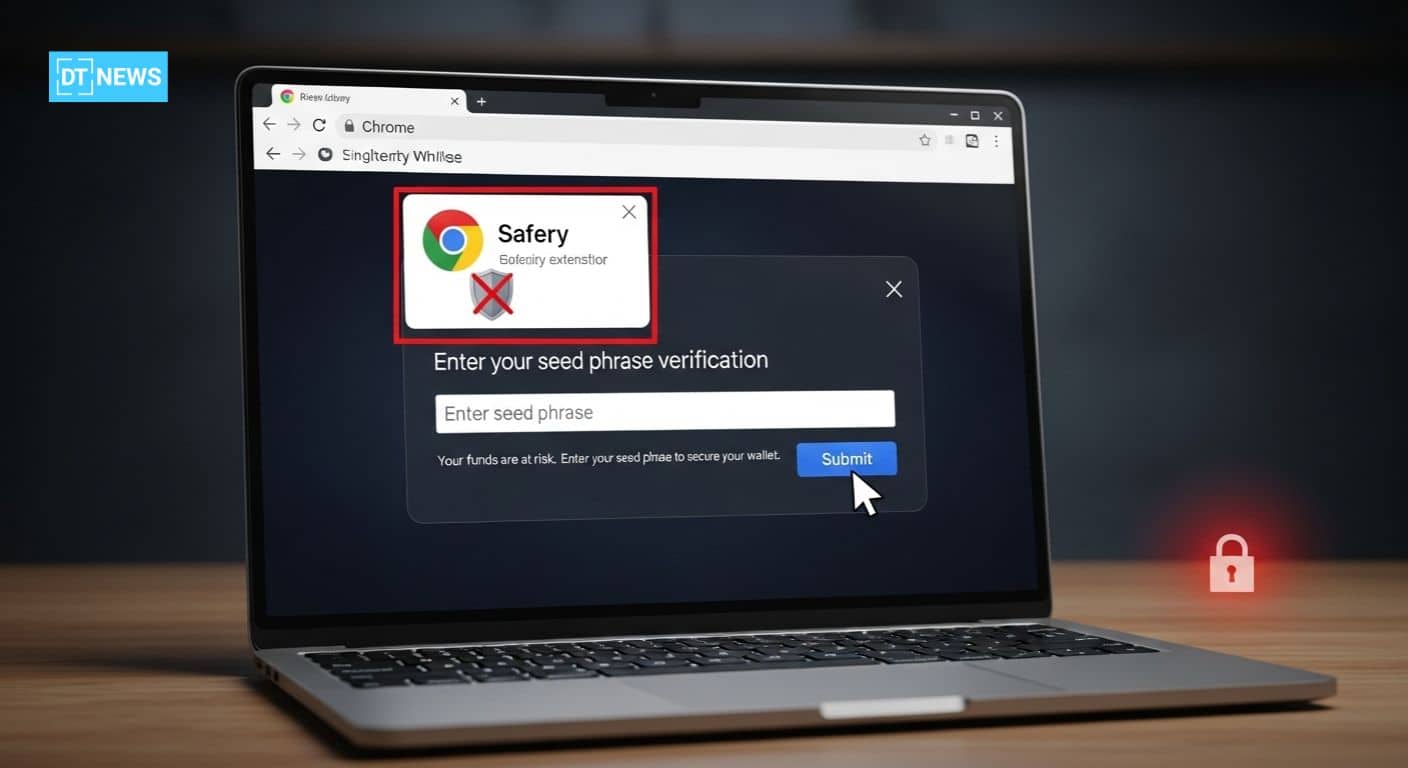
The Stealth Attack: Sui Encodes The Seed Phrase
Upon installation, Safery didn’t call the command-and-control server to transfer data. Instead, as Socket’s Threat Research Team discovered, It encoded the seed phrase, the 12- or 24-word recovery phrase used to restore a wallet on its native blockchain in synthetic Sui-style blockchain addresses.
The extension then sent a very small number of SUI tokens (like 0.000001 SUI) to those manipulated addresses from wallets owned by the attacker.
By observing these transactions on the Sui blockchain and decoding the recipient addresses, threat actors would be able to determine the user’s full seed phrase.
Socket’s reverse engineering protocol revealed that each word in the seed phrase would be translated to its index in a standard BIP-39 list and then packed into a hex string, padded and interpreted as a fake Sui address.
This sidestepped classic network calls or suspicious-looking HTTP traffic, as the exfiltration “occurred” on the blockchain.
Why It Went on So Long: Failures in Chrome Store Vetting
Part of how Safery reached so high in the Web Store ranks has to do with how Chrome’s Extension marketplace is set up.
With the store’s algorithm heaving in favour of install count, review velocity, and average rating rather than deep security vetting. Since Safery generated fake 5-star reviews so quickly, it started to gain traction.
Its description was polished and its permissions appeared routine, allowing it to slip past Google’s more aggressive security checks.
Even after researchers raised an alarm about the threat, the removal wasn’t immediate.
According to security teams, the fact that Safery’s activity did not include suspicious on-chain behavior but rather presence on-chain and no peculiar external network-related actions, had made conventional malware detection mechanisms less applicable.
How Users Were Warned and What They Can Do
Socket and several cybersecurity outlets raised red flags as soon as they discovered Safery’s behavior pattern.
They encourage users to never input their seed phrases into unfamiliar, or unverified extensions.
Whenever they do install a wallet extension, users should make sure to inspect the publisher’s reputation, see if there is an actual website or GitHub repository and scout reviews for patterns such as common generic praise.
If someone believes there is a chance that they have used Safery or any other similarly malicious extension, experts recommend uninstalling the extension at once, revoking all approvals (ERC-20 or elsewhere), and sweeping funds to a new wallet with a secure model of device.
These steps will limit damage but any wallet touched by Safery is compromised.

A Warning for the Crypto Ecosystem
This vulnerability that led to this chrome wallet scam runs deeper. Browser wallets themselves are fundamentally unsafe. Although they offer ease of use and access to DApps, they expose large attack surfaces.
Mixing UI legitimacy with stealthy on-chain exfiltration allowed the Safery extension to evade conventional anti-malware security mechanisms.
Security researchers are demanding fixes.
Suggestions include automatic flagging of extensions that request seed phrase input, better permissions checks, and for there to be a way of verifying publishers i.e. making sure that a wallet really is from a project whose source has been examined according to standards.
For users, it’s a hard lesson: not every Chrome wallet is secure, and trust should be earned rather than freely given.
Conclusion
The Safery chrome wallet scam is among the most sophisticated crypto malware. By sneaking seed phrases into tiny-size Sui blockchain transactions, the attackers side-stepped conventional detection and constructed an invisible exfiltration channel.
The Chrome Store hacker abused the trust in Chrome Store, had elevated itself from fake reviews and even utilized the blockchain itself to spill private data.
The lesson here for wallet users is obvious: always scrutinize extensions, watch the blockchain traffic and approach seed phrase input with extreme caution.
Glossary
Seed Phrase (Mnemonic): List of 12 or 24 words that can be used as a backup to recover wallet and access funds.
Microtransaction: The smallest of blockchain transactions; in this case, sent to move data elsewhere.
BIP-39: A mnemonic seed phrase standard used by many crypto wallets.
Command-and-Control (C2): A server or infrastructure operated by attackers to which data that has been stolen are transmitted.
RPC (Remote Procedure Call): Protocol by which wallets communicate with blockchain nodes.
Frequently Asked Questions About Chrome Wallet Scam
How did the Safery extension go undetected?
Instead of transmitting data over HTTP, it encoded the secret into seemingly legit Sui blockchain transactions, bypassing common malware detection.
Did the extension impersonate a popular wallet?
No, Safery carved its own path. It wasn’t impersonating MetaMask or an existing brand, which could have made it easier to spot.
If someone used Safery can they get money back?
Recovery is hard if seed phrase were leaked. The best course of action is to transfer their funds to a different wallet with newly generated seed.
How do I know if a wallet extension is safe?
Look for developer reputation, active website or repo, good consistent reviews and whether the extension requests seed phrases in insecure contexts.
Will other blockchains be vulnerable to similar attacks?
Experts caution that this method could be mimicked with other public blockchains, not just Sui.